Enterprise Solutions

QDS will help you grow more efficiently by leveraging cutting-edge, cost-effective IT solutions
Technology is becoming more critical to business success and the market is constantly demanding faster, more efficient services. This means having the right IT solutions at a price that doesn’t break the bank will determine the survival of your business.
To help you deliver fast, efficient services while keeping your costs low, QDS offers a comprehensive range of IT solutions that integrate, consolidate, and simplify operations across your entire IT infrastructure. Regardless of the complexity of your needs, our seasoned technicians have you covered.
Our Enterprise Solutions lead to better business results through:
Enhanced operational efficiency
Our customized solutions and proper integration ensure your teams can work smarter and deliver better services in less time
Resources savings
We’ll help you automate mundane tasks and streamline operations with premium IT solutions at SMB-friendly pricing
Peace of mind
The QDS teams will keep all your solutions running at peak performance 24/7/365 so you can work in confidence and focus on growth
Our comprehensive range of efficiency-boosting, cost-cutting IT solutions include:
Operations and Automation
Our Operations and Automation solutions also let you:
- Activate domain-specific agents in on-premises, private, and public cloud environments
- Keep any cloud, XaaS, or on-premises service optimized and secure
- Drive automated AIOps with machine learning derived from more than 50 patents
- Leverage anomaly detection and predictive analytics
- Fix IT issues fast with chatbots, proven ITSM tools, and over 8,000 runbooks
- Gain interactive and historical analysis of hundreds of metrics from our extensive KPI library
Enterprise Service and Asset Management
By letting our experts keep your IT assets in prime condition, you’ll:
- Avoid costly downtime
- Easily stay compliant with changing regulatory compliance
- Keep your operational costs low, thanks to zero unnecessary repair fees or hasty purchasing decisions
Enterprise Cloud
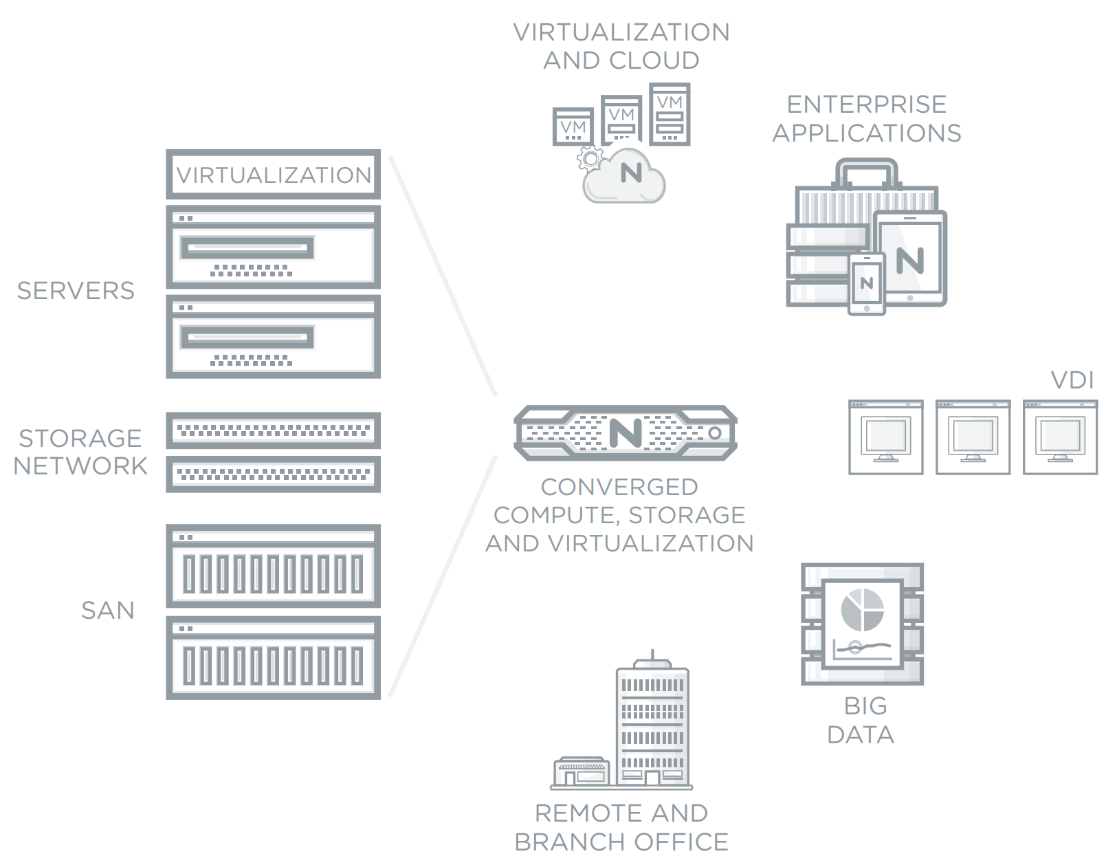
Unified Endpoint Management and Patch Management
Data security is becoming one of the top defining factors for today’s business success. With cybercriminals getting more advanced by the minute, you need automatic, intelligent solutions to keep up with emerging threats — and that’s exactly what QDS can help you achieve.
Our patch management solution allows you to achieve the following via a single user-friendly console
- Stay compliant to ever-changing regulations
- Quickly identify and address the vulnerabilities in your systems
- Automate real-time updates and patches across all devices
- Increase productivity with identity-based management that focuses on users and their needs, not just devices
- And much more
PaaS
PaaS from QDS allows you to:
- Optimize efficiency and application deployments
- Improve security
- Automate mundane tasks and free up your IT staff
- Enjoy seamless integration with your existing cloud or bare-metal servers
- Empower your users with a self-service portal and on-demand resources
- Cut operational costs
Information Analytics
- Actionable insights on market trends and target audience behaviors
- Faster, more informed decision-making
- User-friendly data dashboard that lets you gain real-time visibility over your operations on any device

Media Management
With QDS’s Media Management, you can:
- Automatically capture audio and video files from different sources such as satellite channels, and then edit and deliver them to your desired destinations
- Monitor your social media accounts to stay ahead of market trends
- Transform your big data into actionable decisions
- Manage your content subscribers on an easy-to-use, feature-rich platform

Threat Simulation Platform
With cyeberattacks constantly outsmarting protection schemes, the only way to ensure your business is safe is to test your own defenses before hackers can. QDS helps you do that by using
Threat Simulator, a breach and attack simulation (BAS) platform for network security testing. In addition to identifying your vulnerabilities, we’ll also recommend effective remediation and the latest cybersecurity best practices to keep your entire organization safe from emerging threats.
Application Security
Application Security is a combination of processes, tools, and best practices to keep business applications safe from cyberthreats throughout their entire life cycle. This helps organizations avoid costly data breaches and other kinds of malicious attacks.
QDS provides Micro Focus Application Security solutions, with security testing and management available both on-premises and as-a-service.
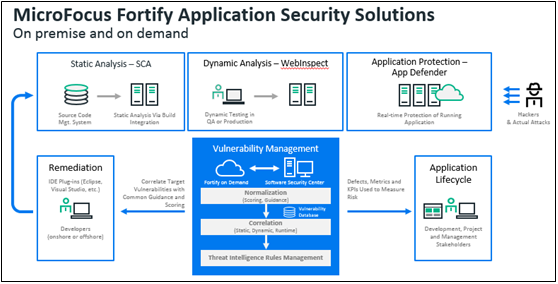
Our Application Security offers a bundle of proven solutions that include:
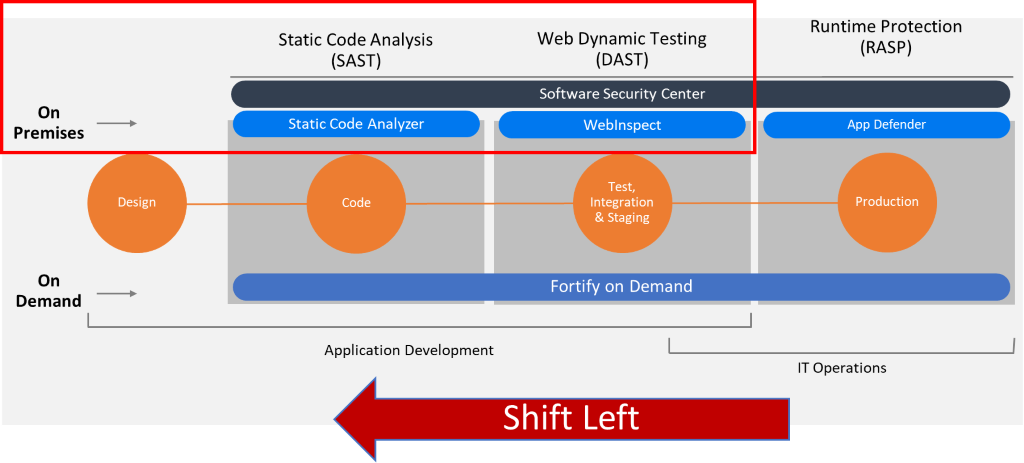
- Fortify Static Code Analyzer – static application security testing (SAST) that pinpoints vulnerabilities early in the software development life cycle
- Fortify WebInspect – dynamic application security testing (DAST) to simulate real-world security attacks on a running application
- Interactive application security testing (IAST) – a combination of our dynamic testing and runtime analysis
- Fortify Application Defender – runtime application self-protection (RASP) that proactively monitors and detects both known and unknown threats
- Fortify on Demand – a simple and quick way to accurately test applications without having to install or manage software or add additional resources
- Mobile Security – a testing methodology that assesses endpoints, networks, and servers
- Software Security Assurance – a centralized management repository that provides visibility on your security performance
- Fortify Software Security Center – a centralized management repository that manages and tracks your security testing activities, giving you a bird’s-eye view of your protection performance

SIEM
Security information and event management (SIEM) is a software solution that aggregates and analyzes activity from many different resources across your entire IT infrastructure.
It then analyzes data to discover trends and detect threats.
QDS offers Elastic SIEM that lets you:
- Easily manage and analyze diverse sets of data across your IT environment
- Effectively block cyberattacks with prebuilt anomaly detection
- Respond to threats fast with a powerful investigation UI and embedded case management
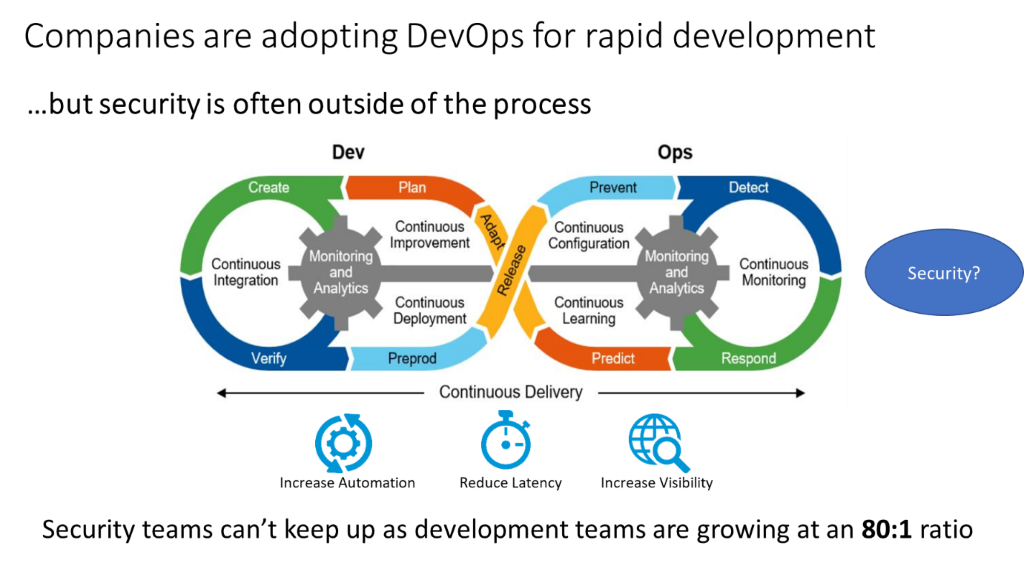
DevOps
Combining development (Dev) and operations (Ops), DevOps streamlines your operations and allows you to deliver better software faster.
With proper integration by QDS, DevOps will help you:
- Improve coordination between different phases of development
- Build and test your applications faster and more effectively
- Respond more effectively to customer needs, and achieve your business goals faster
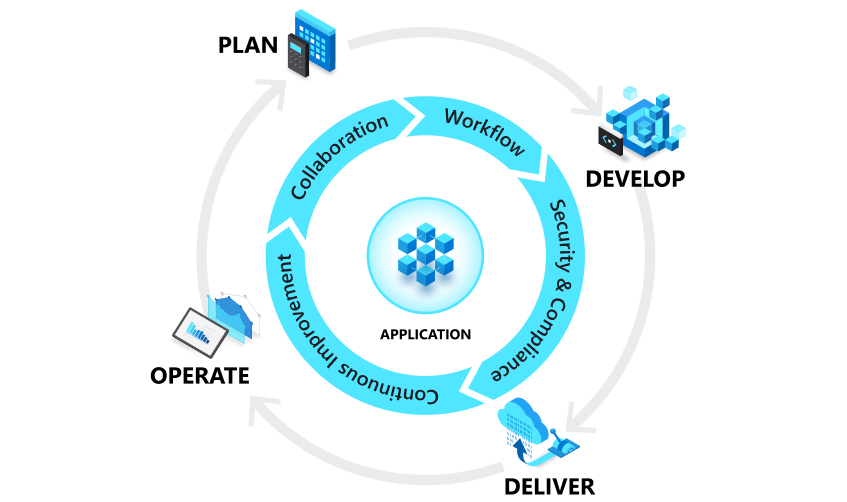
DevSecOps
With expert planning and ongoing management by QDS, your DevSecOps will let you:
- Ensure security throughout application development and deployment
- Help your developers make the most out of DevSecOps with Secure Code Warrior integration and Micro Focus training
- Automate tasks throughout Continuous Integration and Continuous Delivery (CI/CD) pipelines
- SAST with Fortify Static Code Analyzer
- Optimize dynamic application security testing (DAST), runtime application and self-protection (RASP), software composition analysis (SCA), and open source security (OSS)
Robotic Process Automation
With QDS’s Robotic Process Automation, you can:
- Track activities in detailed logs, in real time
- Automate processes without exposing sensitive data, by using unique IDs and role-based credentials
- Save time and cut costs
- Free up your teams so they can focus on growth-generating tasks